Following our initial requirements assessment, we formulate tailored strategies for the client organization and advise on necessary technology enhancements or security transformations. Recognizing that network security applications aren't plug-and-play endeavors, we deploy a team of skilled professionals who configure network security features using top-tier solutions (hardware, software, or cloud-based) in the market. Their role is to continuously monitor and manage these features to ensure the security of both data and the network.
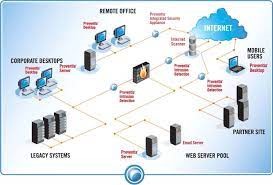
Perimeter security
We assist organizations in safeguarding their network perimeters against malicious actors. Through our consultative approach, we guide customers in making informed choices regarding cybersecurity measures, including options like Next-Generation Firewalls, Intrusion Prevention Systems, Web Application Firewalls, and DDoS protection

Endpoint security
The rise of a mobile workforce, along with a proliferation of devices and evolving threat landscapes, has heightened the demand for endpoint protection. We specialize in helping organizations secure their endpoints through the provision of AI-driven, responsive, user-friendly Next-Generation Endpoint Protection Tools, offering clear visibility and ease of management.

Privileged Access Management
At the heart of identity security lies PAM, a concept now widely acknowledged by analysts and IT leaders as pivotal in safeguarding enterprise resources and users within an environment where the traditional perimeter is vanishing, and work can occur from virtually anywhere
What Dalhyd can do
From strategic planning and project execution to ongoing support and optimization, we are committed to helping you achieve your goals. We offer guidance, innovative solutions, and the latest technologies to enhance your operational efficiency, competitiveness, and overall performance. Our team can assist in managing complexities, mitigating risks, and leveraging opportunities that arise in your industry.

